Article
Active Exploitation of File Transfer Vulnerabilities
Apr 22, 2025
Cyber Threats
At Arete
Cybersecurity Trends

Threat actors are actively exploiting two critical vulnerabilities in CrushFTP and Gladinet’s CentreStack and Triofox products, leading to data exfiltration and extortion. CrushFTP, a managed file transfer solution, is vulnerable to an authentication bypass vulnerability designated CVE-2025-31161. The flaw is simple to exploit, and public exploit code is readily available, increasing risk for organizations that use the platform. Meanwhile, Gladinet’s CentreStack and Triofox products, both file-sharing and remote access platforms, are impacted by a critical remote code execution (RCE) vulnerability stemming from a hardcoded key in its configuration. This flaw (CVE-2025-30406) allows attackers to forge payloads and execute arbitrary code on the server.
What’s Notable and Unique
CVE-2025-31161 is a critical vulnerability affecting CrushFTP v10 and v11 and allows unauthenticated attackers to temporarily authenticate as any user, including administrators, leading to full server compromise. Over 1,500 vulnerable instances have been exposed, and as of April 10, 2025, approximately 440 organizations in North America remain vulnerable.
After exploiting the CrushFTP vulnerability, threat actors often install remote monitoring and management (RMM) tools like AnyDesk and MeshAgent before harvesting credentials. When certain threat actors exploit the vulnerability, they also install a Telegram bot to exfiltrate telemetry from infected hosts.
CVE-2025-30406 is a deserialization vulnerability in CentreStack and Triofox caused by the use of a hardcoded or weakly protected ‘machineKey’ in the IIS ‘web.config’ file, which secures ASP.NET ViewState data. If an attacker can obtain or predict this key, they can forge ViewState payloads that pass integrity checks and trigger deserialization, potentially resulting in remote code execution.
Upon successful exploitation, threat actors often deploy a malicious executable, install the MeshCentral remote access tool, and conduct lateral movement within the network. The vulnerable Triofox product is commonly used by managed service providers (MSPs), posing a serious threat to MSPs and their customers.
Analyst Comments
Overlaps in post-exploit techniques of CVE-2025-30406 (CentreStack and Triofox) and CVE-2025-31161 (CrushFTP), indicate potentially coordinated threat activity or shared attacker infrastructure. Threat actors have installed MeshCentral and used IP address 2.58.56[.]16 for post-exploitation communication in incidents after the exploit of both vulnerabilities. However, based on observed behavior and the ease of exploitation, multiple threat actors are likely exploiting these vulnerabilities. At least one threat actor, KillSec, has publicly claimed exploitation and exfiltration by leveraging the CrushFTP vulnerability. Arete has observed other threat actors extort victims after allegedly exploiting the CrushFTP vulnerability.
The CrushFTP vulnerability has been exploited since March 31, 2025, so any organizations using a vulnerable version of CrushFTP that have not updated should assess for potential unauthorized access and exfiltration. Organizations using a vulnerable version of CrushFTP can take two actions to remediate the vulnerability: upgrade to version 10.8.4 or version 11.3.1 or enable a DMZ proxy instance. Applying the patch will not remove the access of any threat actors who have already exploited the vulnerability and created a new valid user account for the application. For organizations affected by the CentreStack and Triofox vulnerability, an updated version was released by the company that resolves the vulnerability and generates a new machine key.
Sources
Back to Blog Posts
Article
Mar 3, 2026
ClickFix Campaign Delivers Custom RAT
Security researchers identified a sophisticated evolution of the ClickFix campaign that aims to compromise legitimate websites before delivering a five-stage malware chain, culminating in the deployment of MIMICRAT. MIMICRAT is a custom remote access trojan (RAT) written in the C/C++ programming language that offers various capabilities early in the attack lifecycle. The attack begins with victims visiting compromised websites, where JavaScript plugins load a fake Cloudflare verification that tricks users into executing a malicious PowerShell script, further displaying the prominence and effectiveness of ClickFix and its user interaction techniques.
Not Your Average RAT
MIMICRAT displays above-average defense evasion and sophistication, including:
A five-stage PowerShell sequence beginning with Event Tracing for Windows and Anti-Malware Scan Interface bypasses, which are commonly used in red teaming for evading detection by EDR and AV toolsets.
The malware later uses a lightweight scripting language that is scripted into memory, allowing malicious actions without files that could easily be detected by an EDR tool.
MIMICRAT uses malleable Command and Control profiles, allowing for a constantly changing communication infrastructure.
The campaign uses legitimate compromised infrastructure, rather than attacker-owned tools, and is prepped to use 17 different languages, which increases global reach and defense evasion.
Analyst Comments
The ClickFix social engineering technique remains an effective means for threat actors to obtain compromised credentials and initial access to victim environments, enabling them to deploy first-stage malware. Coupled with the sophisticated MIMICRAT RAT, the effectiveness of this campaign could increase. Arete will continue monitoring for changes to the ClickFix techniques, the deployment of MIMICRAT in other campaigns, and other pertinent information relating to the ongoing campaign.
Sources
MIMICRAT: ClickFix Campaign Delivers Custom RAT via Compromised Legitimate Websites
Read More
Article
Feb 20, 2026
Threat Actors Leveraging Gemini AI for All Attack Stages
State-backed threat actors are leveraging Google’s Gemini AI as a force multiplier to support all stages of the cyberattack lifecycle, from reconnaissance to post-compromise operations. According to the Google Threat Intelligence Group (GTIG), threat actors linked to the People’s Republic of China (PRC), Iran, North Korea, and other unattributed groups have misused Gemini to accelerate target profiling, synthesize open-source intelligence, identify official email addresses, map organizational structures, generate tailored phishing lures, translate content, conduct vulnerability testing, support coding tasks, and troubleshoot malware development. Cybercriminals are increasingly exploring AI-enabled tools and services to scale malicious activities, including social engineering campaigns such as ClickFix, demonstrating how generative AI is being integrated into both espionage and financially motivated threat operations.
What’s Notable and Unique
Threat actors are leveraging Gemini beyond basic reconnaissance, using it to generate polished, culturally nuanced phishing lures and sustain convincing multi-turn social engineering conversations that minimize traditional red flags.
In addition, threat actors rely on Gemini for vulnerability research, malware debugging, code generation, command-and-control development, and technical troubleshooting, with PRC groups emphasizing automation and vulnerability analysis, Iranian actors focusing on social engineering and malware development, and North Korean actors prioritizing high-fidelity target profiling.
Beyond direct operational support, adversaries have abused public generative AI platforms to host deceptive ClickFix instructions, tricking users into pasting malicious commands that deliver macOS variants of ATOMIC Stealer.
AI is also being integrated directly into malware development workflows, as seen with CoinBait’s AI-assisted phishing kit capabilities and HonestCue’s use of the Gemini API to dynamically generate and execute in-memory C# payloads.
Underground forums show strong demand for AI-powered offensive tools, with offerings like Xanthorox falsely marketed as custom AI but actually built on third-party commercial models integrated through open-source frameworks such as Crush, Hexstrike AI, LibreChat-AI, and Open WebUI, including Gemini.
Analyst Comments
The increasing misuse of generative AI platforms like Gemini highlights a rapidly evolving threat landscape in which state-backed and financially motivated actors leverage AI as a force multiplier for reconnaissance, phishing, malware development, and post-compromise operations. At the same time, large-scale model extraction attempts and API abuse demonstrate emerging risks to AI service integrity, intellectual property, and the broader AI-as-a-Service ecosystem. While these developments underscore the scalability and sophistication of AI-enabled threats, continued enforcement actions, strengthened safeguards, and proactive security testing by providers reflect ongoing efforts to mitigate abuse and adapt defenses in response to increasingly AI-driven adversaries.
Sources
GTIG AI Threat Tracker: Distillation, Experimentation, and (Continued) Integration of AI for Adversarial Use
Read More
Article
Feb 12, 2026
2025 VMware ESXi Vulnerability Exploited by Ransomware Groups
Ransomware groups are actively exploiting CVE‑2025‑22225, a VMware ESXi arbitrary write vulnerability that allows attackers to escape the VMX sandbox and gain kernel‑level access to the hypervisor. Although VMware (Broadcom) patched this flaw in March 2025, threat actors had already exploited it in the wild, and CISA recently confirmed that threat actors are exploiting CVE‑2025‑22225 in active campaigns.
What’s Notable and Unique
Chinese‑speaking threat actors abused this vulnerability at least a year before disclosure, via a compromised SonicWall VPN chain.
Threat researchers have observed sophisticated exploit toolkits, possibly developed well before public disclosure, that chain this bug with others to achieve full VM escape. Evidence points to targeted activity, including exploitation via compromised VPN appliances and automated orchestrators.
Attackers with VMX level privileges can trigger a kernel write, break out of the sandbox, and compromise the ESXi host. Intrusions observed in December 2025 showed lateral movement, domain admin abuse, firewall rule manipulation, and staging of data for exfiltration.
CISA has now added CVE-2025-22225 to its Known Exploited Vulnerabilities (KEV) catalog, underscoring ongoing use by ransomware attackers.
Analyst Comments
Compromise of ESXi hypervisors significantly amplifies operational impact, allowing access to and potential encryption of dozens of VMs simultaneously. Organizations running ESXi 7.x and 8.x remain at high risk if patches and mitigations have not been applied. Therefore, clients are recommended to apply VMware patches from VMSA‑2025‑0004 across all ESXi, Workstation, and Fusion deployments. Enterprises are advised to assess their setups in order to reduce risk, as protecting publicly accessible management interfaces is a fundamental security best practice.
Sources
CVE-2025-22225 in VMware ESXi now used in active ransomware attacks
The Great VM Escape: ESXi Exploitation in the Wild
VMSA-205-004: VMware ESXi, Workstation, and Fusion updates address multiple vulnerabilities (CVE-205-22224, CVE-2025-22225, CVE-2025-22226)
Read More
Article
Feb 5, 2026
Ransomware Trends & Data Insights: January 2026
Although Akira was once again the most active ransomware group in January, the threat landscape was more evenly distributed than it was throughout most of 2025. In December 2025, the three most active threat groups accounted for 57% of all ransomware and extortion activity; in January, the top three accounted for just 34%. Akira’s dominance also decreased to levels more consistent with early 2025, as the group was responsible for almost a third of all attacks in December but just 17% in January.
The number of unique ransomware and extortion groups observed in January increased slightly, to 17, up from 14 in December. It is too early to assess whether this trend will be the new normal for 2026. It is also worth noting that overall activity in January was lower than in previous months, consistent with what Arete typically observes at the beginning of a new year.
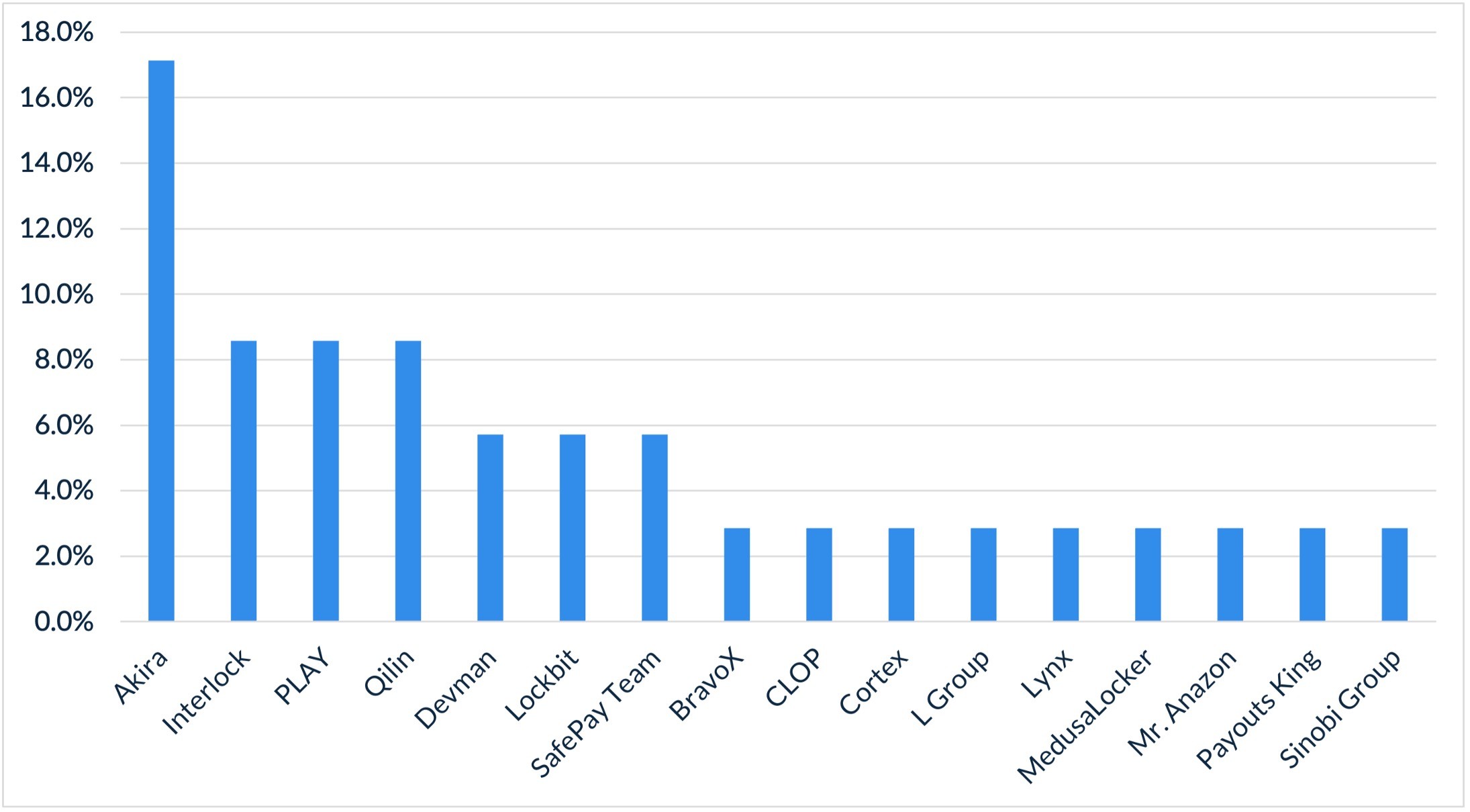
Figure 1. Activity from all threat groups in January 2026
Throughout the month of January, analysts at Arete identified several distinct trends behind the threat actors perpetrating cybercrime activities:
In January, Arete observed the reemergence of the LockBit Ransomware-as-a-Service (RaaS) group, which deployed an updated “LockBit 5.0” variant of its ransomware. LockBit first announced the 5.0 version on the RAMP dark web forum in early September 2025, coinciding with the group’s six-year anniversary. The latest LockBit 5.0 variant has both Windows and Linux versions, with notable improvements, including anti-analysis features and unique 16-character extensions added to each encrypted file. However, it remains to be seen whether LockBit will return to consistent activity levels in 2026.
The ClickFix social engineering technique, which leverages fake error dialog boxes to deceive users into manually executing malicious PowerShell commands, continued to evolve in unique ways in January. One campaign reported in January involved fake Blue Screen of Death (BSOD) messages manipulating users into pasting attacker-controlled code. During the month, researchers also documented a separate campaign, dubbed “CrashFix,” that uses a malicious Chrome browser extension-based attack vector. It crashes the web browser, displays a message stating the browser had "stopped abnormally," and then prompts the victim to click a button that executes malicious commands.
Also in January, Fortinet confirmed that a new critical authentication vulnerability affecting its FortiGate devices is being actively exploited. The vulnerability, tracked as CVE-2026-24858, allows attackers with a FortiCloud account to log in to devices registered to other account owners due to an authentication bypass flaw in devices using FortiCloud single sign-on (SSO). This recent activity follows the exploitation of two other Fortinet SSO authentication flaws, CVE-2025-59718 and CVE-2025-59719, which were disclosed in December 2025.
Source
Arete Internal
Read More