Article
Darkside Ransomware: Caviar Taste on Your Big-Game Budget
Feb 23, 2021
Arete Analysis

Summary
Explore Darkside ransomware, an operation utilizing sophisticated tactics to target high-revenue organizations. Arete’s threat intelligence data reveals high ransom demands, extensive business downtime, and universal data exfiltration.
By all appearances, the proprietors of Darkside ransomware mean business.
With their sights set on organizations with US$4M+ in revenue, they’re about high-value, big-game targets and they’ve got the skills and experience to bring in some big hauls.
The Darkside group demonstrates seasoned experience, polished business acumen, and an ability to quickly respond to both negative and positive stimuli within their sphere of market influence. They exhibit similarities to notable ransomware operations, such as LockBit and REvil, and they take an outwardly aggressive posture toward the security industry, taunting companies like BitDefender and Coveware.
Statistical data on Darkside ransomware from Arete engagements
The information below is based on Darkside events that the Arete IR team has investigated since November 2020. Our incident response and data analytics practices work together to track key data points and collect statistics on variants for every ransomware engagement.
Sectors of clients affected by this threat:
Professional Services | Manufacturing
Average Ransom Demand: US $6,527,402.02
Highest Ransom Demand: US $10,054,804
Lowest Ransom Demand: US$3,000,000
Average business downtime: 5 days
Data exfiltration observed in 100 percent of cases
Key observations
Based on the Arete Cyber Threat Intelligence (CTI) team’s assessments:
Darkside ransomware operators are likely conducting long-tail reconnaissance of the victim environment for up to two (2) weeks prior to deploying their payloads.
The earliest known point of malicious activity for a select event was noted when forensic discovery indicated installation of the MetaSploit framework on the victim’s domain controller fifteen (15) days prior to enterprise-wide, automated deployment of Darkside.
Yes, we expect Darkside to be big-game hunters. Forbes quoted them as saying they will target “only those who can afford to pay.” Their recruitment advertisements echo this assertion.
Darkside proprietors and operators come from an established pedigree.
They are transparent in their description of operational mistakes and they renumerate operators for lost revenue.
They taunt BitDefender and Coveware directly with aggressive and forthright assertions of their intent.
As recently as December 27, 2020, a Russian-speaking cybercriminal actor using the handle ‘darksupp’ invited media outlets and data recovery organizations to follow a new “Press Center” section at the Darkside “name-and-shame” leak site. Darksupp allegedly stated that this press center would enable media and recovery firms to ask questions about recent attacks while also giving recovery organizations access to a dedicated chat room, where they could enroll in a “loyalty program” for discounts on data decryption.
The group has underwritten their aspirations with a substantial surety bond (approx. US$350k) and assert that they are willing to increase their guarantee to inspire further confidence in the right partners.
Their first and now exclusive appearance on XSS (reboot of DamageLab) along with exploitation of their endorsements/acceptance from known Russian-speaking actors underpins the Arete CTI team’s current assessment of their maturity and client knowledge.
On November 10, 2020, a Russian-speaking cybercriminal actor using the handle ‘darksupp’ announced the launch of an official recruitment effort for affiliates to participate in the Darkside Ransomware-as-a-Service (RaaS) affiliate program.
Darksupp received a forum-public favorable review on XSS from actor Quake3 (aka LockBit), proprietor of the LockBit RaaS platform.
The proprietor(s) behind the ‘darksupp’ persona tout seasoned experience with and feature influence from notable ransomware operations, such as LockBit and REvil.
Darkside operator affiliates are likely using Whitebit (e.g., Whitebit[.]com) to cash out, given observed wallet transactions and ledger analysis by Arete.
Detailed information
On August 8, 2020, operators of the Darkside ransomware announced their malware in a press release on the dark web. They stated that they had created their ransomware because they could not find the perfect product for their needs and had made millions of dollars by partnering with other well-known ransomware groups. In the same release, they also said they would not be targeting the healthcare, education, non-profit, and government sectors.
On November 11, 2020, Darkside announced their RaaS model, inviting partners and affiliates to work with them. They also announced the development of a distributable data storage system, calling out the use of servers in Iran and unrecognized republics to prevent victim organizations from taking down their operations.
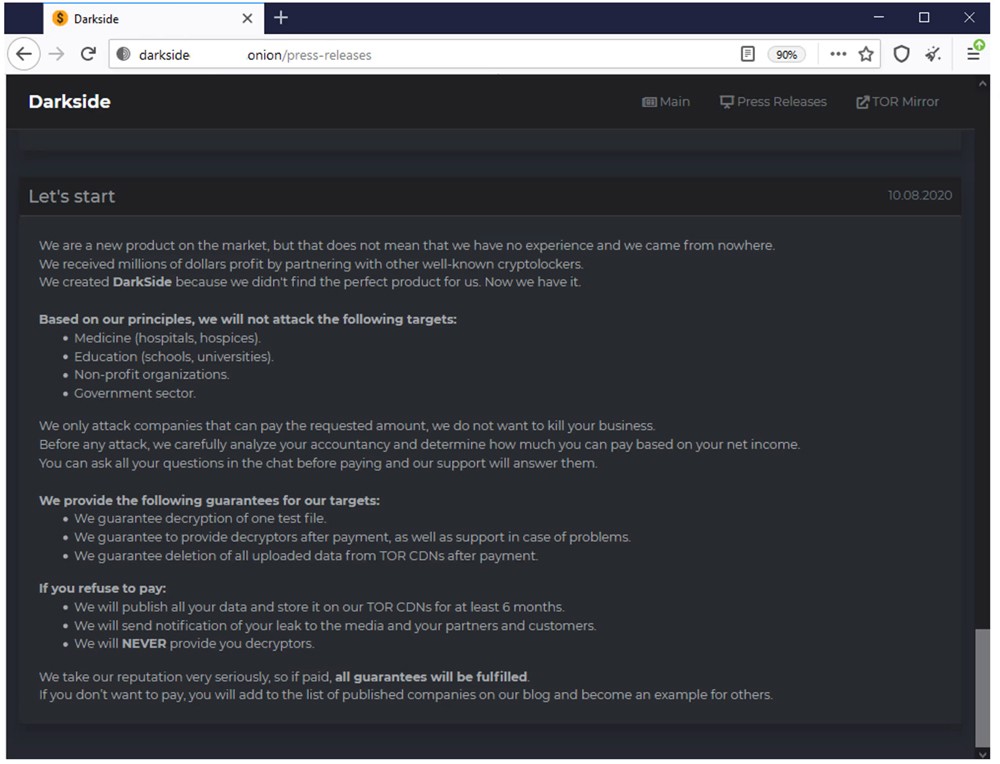
Figure 1. Darkside announces their service.
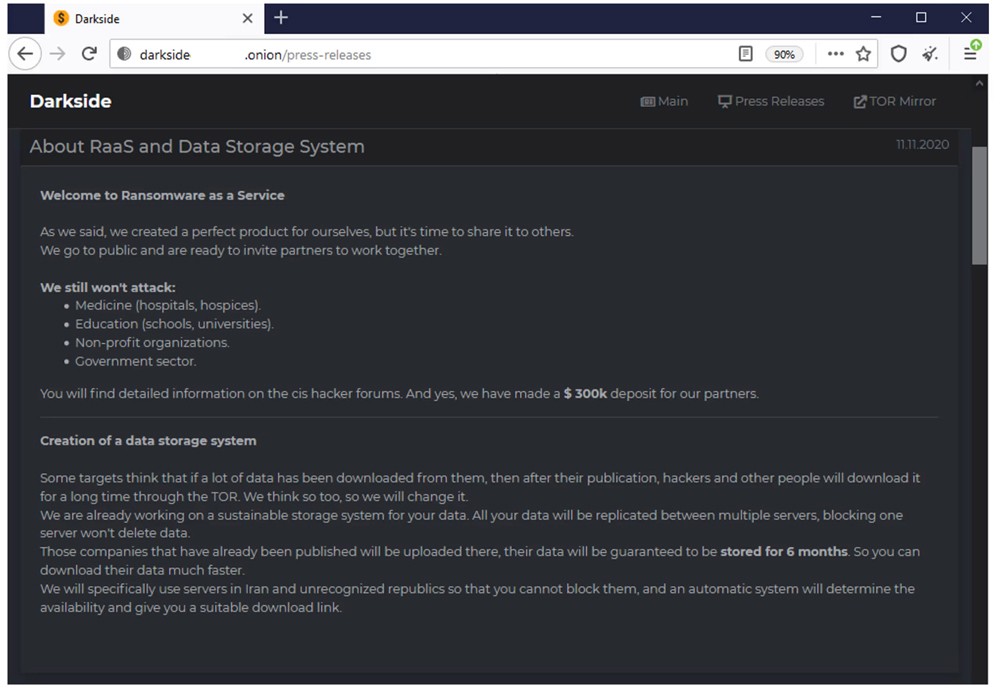
Figure 2. Darkside announcement of their RaaS product, distributed storage system, and invitation to partners and affiliates to work with them.
After this announcement, multiple news outlets began reporting that the group was using servers in sanctions countries like Iran. In response, the Darkside group updated their storage announcement on November 15, 2020, stating:
The storage system is still in the planning stages and has not yet launched.
They are not citizens of Iran, and leaked company data is not and will not be hosted in Iran.
They are still considering where to host the leaked data, but it would not be in a region on the sanctions list.
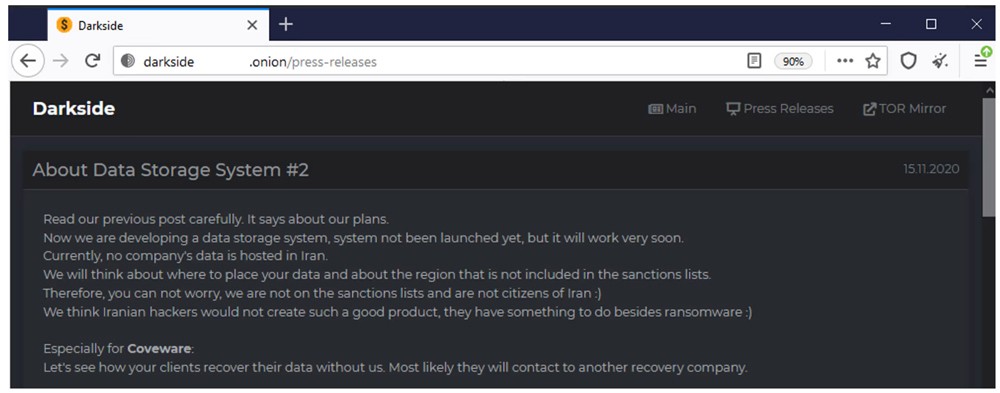
Figure 3. Darkside makes an updated announcement, that they will think where to host leaked data on servers that are not in sanctions countries.
The above business model makes total sense from the threat actors’ perspective. If the data were stored on servers in regions on the U.S. Treasury Department’s Office of Foreign Asset Control (OFAC) sanctions list, the actors would be unable to obtain ransom payments from victims.
The Arete CTI team and other researchers in the community found that the group has been advertising their services on well-known Russian hacker forums, with posts written in Russian.
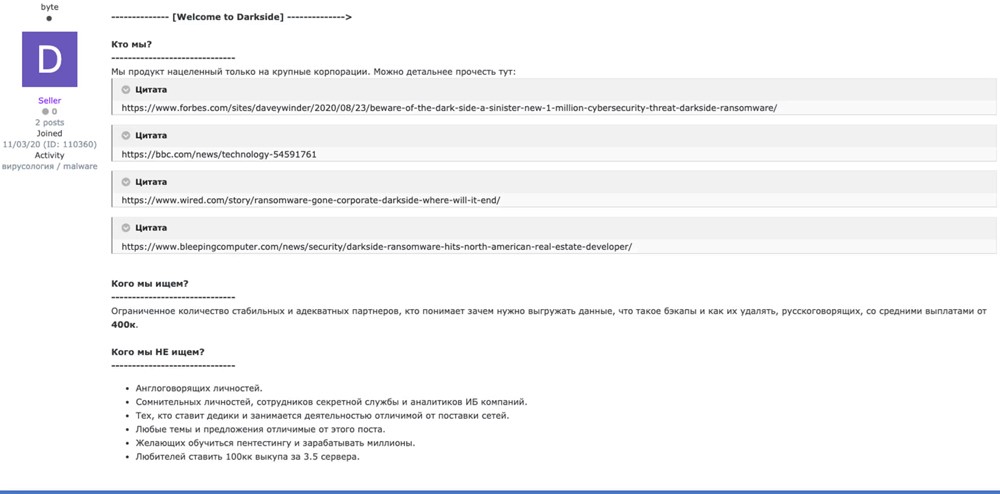
Figure 4. Darkside group advertising on a well-known hacking forum (Source: SentinelOne)
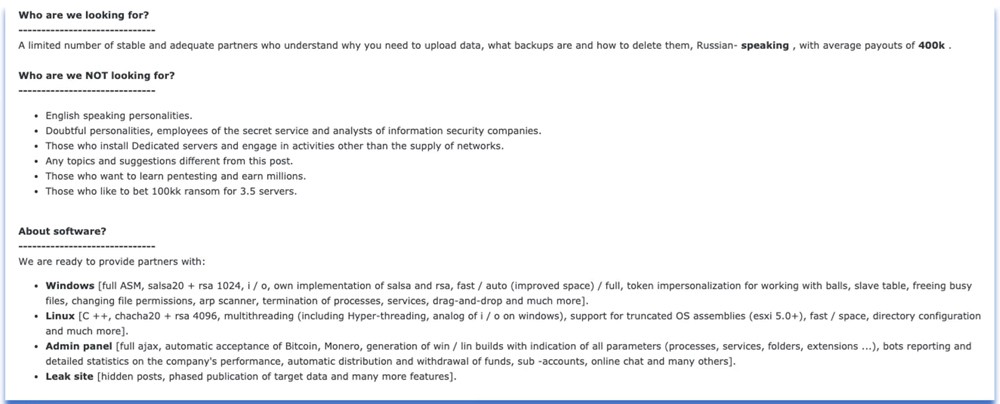
Figure 5. A Google translation of Darkside advertisement on a well-known Russian hacking forum (Source: SentinelOne)
Based on language analysis, a native Russian-language speaker wrote the posts. What’s more, the group’s ransomware is designed to avoid infecting systems in Commonwealth of Independent States (CIS) countries, including Russia. In the past, other Eastern European threat actor groups have done the same to try to avoid getting in trouble with local law enforcement agencies. The Arete CTI team also conducted blockchain analysis of previous ransom payments and did not find any ties between sanctioned entities/money service businesses (MSBs) and Darkside money-laundering operations.
As leaders in the community and especially in the current COVID-19 climate, we need to join forces to properly inform the public without causing worldwide panic and help ensure our clients’ quick recovery from attacks and return to normal business operations. If a company were to make a rash decision about ransom payments based on negligent reporting, it could prevent file restoration and ultimately, shutter a business and cost employees their livelihood.
Darkside high-level technical overview
While tactics, techniques, and procedures (TTPs) may vary amongst operators, it’s important to note that Darkside caters to semi-exclusive affiliates, likely of Russian or Eastern European origin. They likely pool their technical experience — both successes and failures — from this exclusive cultural enclave to orchestrate their intrusions and execute on their objective as outlined below:
Darkside ransomware is primarily geared toward Windows systems, however, the proprietor ‘darksupp’ claims the ability to develop payloads that also target Linux OS variants.
We have observed the builder module screens for the control panel, and we are aware of the existence of Linux ELF-executable payloads. We assess this to be true, with high confidence.
Given observed use of MetaSploit and potentially other Offensive Security Tool (OST) frameworks — always contingent on operator/affiliate preference — it’s likely that Darkside ransomware operators leverage these same tools to enumerate vulnerabilities of victim networks, where externally facing systems of interest are exposed, to establish initial access.
We observed actors pivoting from having Administrator RDP sessions on the Domain Controller, to accessing another privileged account to access a file server. Thus, it’s highly likely that their two weeks in the environment afforded them precision-targeting abilities. They took their time hunting.
On November 25, 2020, ‘darksupp’ claimed to have launched a content delivery network (CDN) for storing and delivering compromised data exfiltrated from victims of Darkside ransomware. The actor also claimed to be developing a second version of the ransomware and intends to provide support for distribution using dynamic-link library (.dll) and PowerShell scripts (.ps1) for deployment.
We have observed Darkside operators manually enumerating and exfiltrating data using a combination of RDP access and their own copy of QTBrowser, 7zip. This culminates in a direct upload of files to both PrivatLab and MegaUpload cloud hosting, under cover of Web/HTTPS sessions, which are difficult to sift in many cases for less mature organizations. \
This manual methodical exfiltration occurred over the span of several hours.
7zip archives were named after data/folder names enumerated and temporarily stored in root temp directory (e.g., C:Temp, C:Temp1, C:Temphr{archive}.7z).
We observed Darkside payload (e.g., azure_agent.exe.exe) staged on the domain controller in a network-shareable folder (e.g., C:WindowsIMEazure), followed by the establishment of a scheduled task (e.g., WindowsSYSVOLdomainPolicies{L0NGMGU1D}UserPreferencesScheduledTasks) set with Group Policy and instructing hosts to obtain and execute the payload. This resulted in a fully automated enterprise-wide deployment less than 24 hours after data was exfiltrated.
Security Recommendations
Implement a sophisticated endpoint detection and response (EDR) solution that will rely on behavior analysis — not just malware signatures — and have tamper-proof capabilities.
Implement multifactor authentication (MFA).
Implement an email security solution to detect and protect against known and unknown threats.
Hunt for unusual remote desktop protocol (RDP) connections.
Use Group Policy Software Restriction Policies (SRP) to prevent users from executing Windows executable filetypes (e.g., .exe, .dll, .hta, .bat, .scr) from the AppDataLocalTemp path of Office365, Microsoft Word, Excel, and Outlook. Alternatively, also inspect C:Users[current user]AppDataRoamingMicrosoft as it’s another popular method that achieves the same results.
Implement and regularly test an off-site backup solution.
Appendix
Indicator | Role |
|---|---|
C:\Windows\IME\azure | File path of DC where Darkside payload was staged. |
F:\temp | File path of staged 7zip archives (.7z) prior to exfiltration |
F:\temp1 | File path of staged 7zip archives (.7z) prior to exfiltration |
F:\temphr | File path of staged 7zip archives (.7z) prior to exfiltration |
Windows\SYSVOL\domain\Policies\{LONGMGU1D}\User\Preferences\ScheduledTasks | Path of Scheduled Task on Domain Controller for deployment of Darkside payload via Group Policy. |
Indicator | Role |
|---|---|
azure_agent.exe.exe | Darkside Payload |
README.3a43168b.TXT | Darkside Ransomware Note – README.{random_string}.TXT |
enc.exe | Darkside Payload |
idfoodsf.exe | Darkside Payload |
Indicator | Role |
|---|---|
6d134cdf470f03707ad481b617e67b9018f92f72a0e2fb3e6cc9f2ab17ac1439 | Darkside Payload |
06cfe7f5d88e2f7adda6d8333ca8b302debb22904c68a942188be5730e9b3c8 | Darkside Payload |
243dff0fc80a049f4fb3729f8b8def0fce29768f345c88ee1069e22b0ae60 | Darkside Payload |
0839aabe5fd63b16844a27b3c586c02a044d119010a1a40ee4035501c34eae0d | Darkside Payload |
Indicator | Role |
|---|---|
www[.]privatelab[.]com | Manual Data Exfiltration – Cloud Upload |
www[.]mega[.]nz | Manual Data Exfiltration – Cloud Upload |
Bitcoin Wallet Address
bc1qkk8z69uxkrxdeuwlkvlk89p7qnr6cefa4aeq7p
Leak Site
hxxps://Darksidedxcftmqa[.]onion
Complete advertisement from the Darkside group on a popular Russian hacking forum (Full translation from Russian to English)
————- [Welcome to Darkside] ————–> Кто мы? ——————————
Мы продукт нацеленный только на крупные корпорации. Можно детальнее прочесть тут: https://www.forbes.com/sites/daveywinder/2020/08/23/beware-of-the-dark-side-a-sinister-new-1-million-cybersecurity-threat-Darkside-ransomware/ https://bbc.com/news/technology-54591761https://www.wired.com/story/ransomware-gone-corporate-Darkside-where-will-it-end/ https://www.bleepingcomputer.com/news/security/Darkside-ransomware-hits-north-american-real-estate-developer/
Кого мы ищем?
——————————
Ограниченное количество стабильных и адекватных партнеров, кто понимает зачем нужно выгружать данные, что такое бэкапы и как их удалять, русскоговорящих, со средними выплатами от 400к. Кого мы НЕ ищем?
——————————
Англоговорящих личностей.
Сомнительных личностей, сотрудников секретной службы и аналитиков ИБ компаний.
Тех, кто ставит дедики и занимается деятельностью отличимой от поставки сетей.
Любые темы и предложения отличимые от этого поста.
Желающих обучиться пентестингу и зарабатывать миллионы.
Любителей ставить 100кк выкупа за 3.5 сервера.
О софте?
——————————
Мы готовы предоставить партнерам:
Windows [full ASM, salsa20 + rsa 1024, i/o, собственная реализация salsa и rsa, fast / auto (улучшенный space) / full, имперсонализация токена для работы с шарами, раб столом, освобождение занятых файлов, изменение прав на файлы, arp scanner, завершения процессов, сервисов, drag-and-drop и много другого].
Linux [C++, chacha20 + rsa 4096, многопоточен (в том числе Hyper-threading, аналог i/o на windows), поддержка урезанных сборок ос (esxi 5.0+), fast / space, настройка каталогов и много другого].
Админ панель [full ajax, автоматический прием Bitcoin, Monero, генерация win / lin билдов с указанием всех параметров (процессы, сервисы, папки, расширения…), отстук ботов и детальная статистика по результативности компании, автоматическое распределение и вывод средств, саб–аккаунты, онлайн чат и множество другого].
Leak site [скрытые посты, поэтапная публикация данных таргета и еще множество функционала].
Все решения уже проверены и доделаны, мы сами работаем своим софтом и не писали его на продажу / аренду, в отличие от многих продуктов.То чего нам не хватало в работе с другими партнерскими программами — мы реализовали у себя.
Правила?
——————————
Следующие сферы запрещены:
– Медицина (Больницы, госпитали).
– Образование (Университеты, школы).
– Государственный сектор (муниципалитеты, любые гос органы).
– Некоммерческие организации (благотворительные фонды, ассоциации).Запрещены любые действия, которые наносят репутационный урон имиджу продукта.
Запрещена любая работа по СНГ (в том числе Грузии, Украине).
Запрещена передача аккаунта третьим лицами.
Какой процент?
——————————
От 25% до 10%. В софте динамическая система рейта. Чем больше выплата, тем меньше % партнерки и наоборот.Так же возможен стабильный рейт, это обсуждается. Как попасть?
——————————
Пройти собеседование, показать свою работу и выплаты, ответить на необходимые вопросы.Но для начала написать в ЛС. При этом указать:
Свой опыт работы.
С какими партнерскими программами работали.
Диапазон сумм выкупа. Минимум, максимум, средняя.
Работаете сами или в команде.
TOX или jabber.
Если вам не ответили, то вы не подошли, спамить в теме не нужно.
Рассматриваем ли мы доступы в сети?
——————————
Да, USA от 400kk, с предложениями можно отписать в ЛС, написав сайт, сферу деятельности компании и контакт. Если компания интересна – с вами свяжутся. Какие гарантии?
——————————
Депозит в 20 BTC (~305k на момент написания) на xss.is. Если у вас будут супер предложения, мы с удовольствием его поднимем, вплоть до 1кк и более.
Translation to English:
Who are we looking for?
——————————
A limited number of stable and adequate partners who understand the importance of exfiltrating data, awareness of backups and how to delete them, Russian-speaking, with average payouts of 400k.
Who are we NOT looking for?
——————————
English-speaking personalities.
Suspicious individuals, employees of the secret service and analysts of information security companies.
Those who only setup RDP access or do other things other than deploy on networks.
Any topics and suggestions different from this post.
Those who want to learn pen-testing and earn millions.
Those who think they can demand US$100M in ransom for 3.5 servers. About software?
——————————
We are ready to provide partners with:
Windows payloads [full ASM (assembly language), I/O, custom implementation of the Salsa20 and RSA-1024 ciphers, fast / automated / full encryption, token impersonation for accessing shared network drives, process termination to encrypt open files, file permission modification, ARP scanning tool, the drag-and-drop UI/UX features, and much more)
Linux payloads [C++, ChaCha20 + RSA-4096, multithreading (including hyper-threading, an analogue of the Windows I/O system), support of stripped-down OS versions (ESXI 5.0 and up), fast [encryption] / space [overwrite], catalog adjustment, and many other things].
Admin panel [ajax, automatic transaction processing for Bitcoin, Monero, generation of Windows/Linux builds with selectable parameters (processes, services, folders, and extensions), bots will report detailed statistics on the company’s performance, ability to create sub-accounts, online chat and much more].
Leak site [ability to hide posts, allows for detailed disclosures of compromised data, and much more]. All solutions have been tested and we work with our own software and did we did not produce it simply for sale/rent, unlike many products. In our program, we’ve implemented everything we wanted, but did not find in other affiliate programs.
Rules?
——————————
The following areas are prohibited:
Healthcare (clinics and hospitals).
Education (universities and schools).
The public sector (municipal services and public agencies).
Non-profit organizations (charitable foundations and associations).
Any actions that can damage the product reputation are prohibited.
Do not target systems in the CIS (this includes Georgia and Ukraine).
Sharing accounts is not allowed.
What’s the percentage/share of profits?
——————————
From 25% to 10%. The software has a dynamic rate system. The higher the payout, the lower the% of the affiliate program and vice versa.
A stable rate is also possible, this is being discussed.
How to get?
——————————
Pass an interview, show your work and payments, answer the necessary questions. First, send us a message. Indicate:
Your previous experience.
What other programs you’ve worked.
Your range of previous closed payments; minimum, maximum, average.
Your preferences on working alone or with a team.
Provide your TOX or Jabber contact.
If we don’t answer you, then you weren’t the right fit, don’t spam us about it in the topic thread. Will we consider network accesses?
——————————
Sure, provided it’s a U.S. company with US$400M+ in revenue.
Solicit your offer for consideration; provide company website, line of business, and your contact details. If we’re interested, we’ll contact you.
What guarantees?
——————————
We made a deposit of 20 BTC (~ 305,000 USD) with forum escrow at XSS. If you make an awesome partnership proposal, we may raise that deposit to 1M+ to instill further confidence.
——————————
Note: Edited for clarity and readability
Back to Blog Posts
Article
Mar 9, 2026
Ransomware Trends & Data Insights: February 2026
After a slight lull in January, Akira and Qilin returned to dominating ransomware activity in February, collectively accounting for almost half of all engagements that month. The rest of the threat landscape remained relatively diverse, with a mix of persistent threats like INC and PLAY, older groups like Cl0p and LockBit, and newer groups like BravoX and Payouts King. Given current trends, the first quarter of 2026 will likely remain relatively predictable, with the top groups from the second half of 2025 continuing to operate at fairly consistent levels month to month.
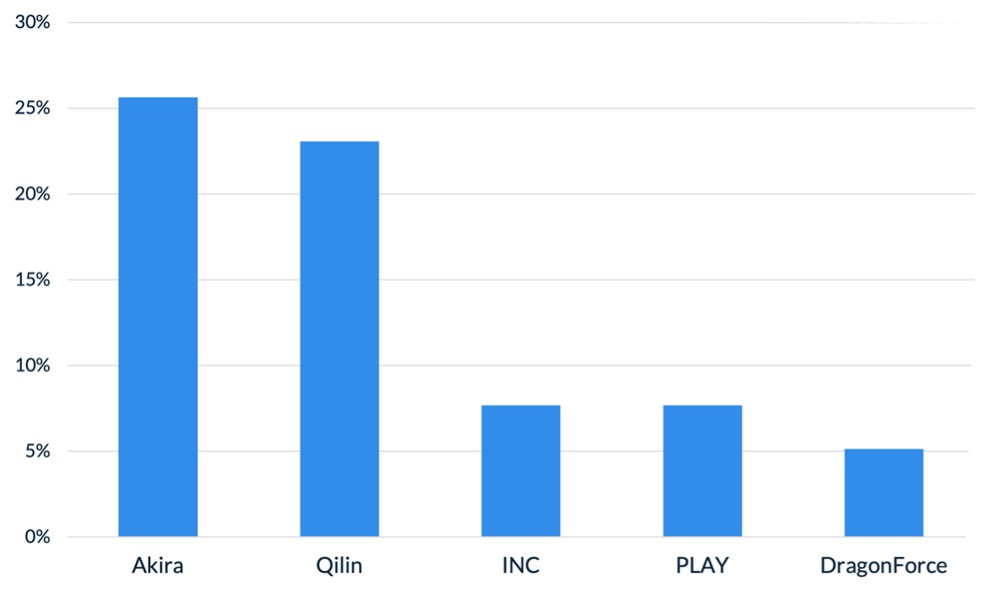
Figure 1. Activity from the top 5 threat groups in February 2026
Throughout the month of February, analysts at Arete identified several trends behind the threat actors perpetrating cybercrime activities:
In February, Arete observed Qilin actively targeting WatchGuard Firebox devices, especially those vulnerable to CVE-2025-14733, to gain initial access to victim environments. CVE-2025-14733 is a critical vulnerability in WatchGuard Fireware OS that allows a remote, unauthenticated threat actor to execute arbitrary code. In addition to upgrading WatchGuard devices to the latest Firebox OS version, which patches the bug, administrators are urged to rotate all shared secrets on affected devices that may have been compromised and may be used in future campaigns.
Reports from February suggest that threat actors are increasingly exploring AI-enabled tools and services to scale malicious activities, demonstrating how generative AI is being integrated into both espionage and financially motivated threat operations. The Google Threat Intelligence Group indicated that state-backed threat actors are leveraging Google’s Gemini AI as a force multiplier to support all stages of the cyberattack lifecycle, from reconnaissance to post-compromise operations. Separate reporting from Amazon Threat Intelligence identified a threat actor leveraging commercially available generative AI services to conduct a large-scale campaign against FortiGate firewalls, gaining access through weak or reused credentials protected only by single-factor authentication.
The Interlock ransomware group recently introduced a custom process-termination utility called “Hotta Killer,” designed to disable endpoint detection and response solutions during active intrusions. This tool exploits a zero-day vulnerability (CVE-2025-61155) in a gaming anti-cheat driver, marking a significant adaptation in the group’s operations against security tools like FortiEDR. Arete is actively monitoring this activity, which highlights the growing trend of Bring Your Own Vulnerable Driver (BYOVD) attacks, in which threat actors exploit legitimate, signed drivers to bypass and disable endpoint security controls.
Sources
Arete Internal
Read More
Article
Mar 3, 2026
ClickFix Campaign Delivers Custom RAT
Security researchers identified a sophisticated evolution of the ClickFix campaign that aims to compromise legitimate websites before delivering a five-stage malware chain, culminating in the deployment of MIMICRAT. MIMICRAT is a custom remote access trojan (RAT) written in the C/C++ programming language that offers various capabilities early in the attack lifecycle. The attack begins with victims visiting compromised websites, where JavaScript plugins load a fake Cloudflare verification that tricks users into executing a malicious PowerShell script, further displaying the prominence and effectiveness of ClickFix and its user interaction techniques.
Not Your Average RAT
MIMICRAT displays above-average defense evasion and sophistication, including:
A five-stage PowerShell sequence beginning with Event Tracing for Windows and Anti-Malware Scan Interface bypasses, which are commonly used in red teaming for evading detection by EDR and AV toolsets.
The malware later uses a lightweight scripting language that is scripted into memory, allowing malicious actions without files that could easily be detected by an EDR tool.
MIMICRAT uses malleable Command and Control profiles, allowing for a constantly changing communication infrastructure.
The campaign uses legitimate compromised infrastructure, rather than attacker-owned tools, and is prepped to use 17 different languages, which increases global reach and defense evasion.
Analyst Comments
The ClickFix social engineering technique remains an effective means for threat actors to obtain compromised credentials and initial access to victim environments, enabling them to deploy first-stage malware. Coupled with the sophisticated MIMICRAT RAT, the effectiveness of this campaign could increase. Arete will continue monitoring for changes to the ClickFix techniques, the deployment of MIMICRAT in other campaigns, and other pertinent information relating to the ongoing campaign.
Sources
MIMICRAT: ClickFix Campaign Delivers Custom RAT via Compromised Legitimate Websites
Read More
Article
Feb 20, 2026
Threat Actors Leveraging Gemini AI for All Attack Stages
State-backed threat actors are leveraging Google’s Gemini AI as a force multiplier to support all stages of the cyberattack lifecycle, from reconnaissance to post-compromise operations. According to the Google Threat Intelligence Group (GTIG), threat actors linked to the People’s Republic of China (PRC), Iran, North Korea, and other unattributed groups have misused Gemini to accelerate target profiling, synthesize open-source intelligence, identify official email addresses, map organizational structures, generate tailored phishing lures, translate content, conduct vulnerability testing, support coding tasks, and troubleshoot malware development. Cybercriminals are increasingly exploring AI-enabled tools and services to scale malicious activities, including social engineering campaigns such as ClickFix, demonstrating how generative AI is being integrated into both espionage and financially motivated threat operations.
What’s Notable and Unique
Threat actors are leveraging Gemini beyond basic reconnaissance, using it to generate polished, culturally nuanced phishing lures and sustain convincing multi-turn social engineering conversations that minimize traditional red flags.
In addition, threat actors rely on Gemini for vulnerability research, malware debugging, code generation, command-and-control development, and technical troubleshooting, with PRC groups emphasizing automation and vulnerability analysis, Iranian actors focusing on social engineering and malware development, and North Korean actors prioritizing high-fidelity target profiling.
Beyond direct operational support, adversaries have abused public generative AI platforms to host deceptive ClickFix instructions, tricking users into pasting malicious commands that deliver macOS variants of ATOMIC Stealer.
AI is also being integrated directly into malware development workflows, as seen with CoinBait’s AI-assisted phishing kit capabilities and HonestCue’s use of the Gemini API to dynamically generate and execute in-memory C# payloads.
Underground forums show strong demand for AI-powered offensive tools, with offerings like Xanthorox falsely marketed as custom AI but actually built on third-party commercial models integrated through open-source frameworks such as Crush, Hexstrike AI, LibreChat-AI, and Open WebUI, including Gemini.
Analyst Comments
The increasing misuse of generative AI platforms like Gemini highlights a rapidly evolving threat landscape in which state-backed and financially motivated actors leverage AI as a force multiplier for reconnaissance, phishing, malware development, and post-compromise operations. At the same time, large-scale model extraction attempts and API abuse demonstrate emerging risks to AI service integrity, intellectual property, and the broader AI-as-a-Service ecosystem. While these developments underscore the scalability and sophistication of AI-enabled threats, continued enforcement actions, strengthened safeguards, and proactive security testing by providers reflect ongoing efforts to mitigate abuse and adapt defenses in response to increasingly AI-driven adversaries.
Sources
GTIG AI Threat Tracker: Distillation, Experimentation, and (Continued) Integration of AI for Adversarial Use
Read More
Article
Feb 12, 2026
2025 VMware ESXi Vulnerability Exploited by Ransomware Groups
Ransomware groups are actively exploiting CVE‑2025‑22225, a VMware ESXi arbitrary write vulnerability that allows attackers to escape the VMX sandbox and gain kernel‑level access to the hypervisor. Although VMware (Broadcom) patched this flaw in March 2025, threat actors had already exploited it in the wild, and CISA recently confirmed that threat actors are exploiting CVE‑2025‑22225 in active campaigns.
What’s Notable and Unique
Chinese‑speaking threat actors abused this vulnerability at least a year before disclosure, via a compromised SonicWall VPN chain.
Threat researchers have observed sophisticated exploit toolkits, possibly developed well before public disclosure, that chain this bug with others to achieve full VM escape. Evidence points to targeted activity, including exploitation via compromised VPN appliances and automated orchestrators.
Attackers with VMX level privileges can trigger a kernel write, break out of the sandbox, and compromise the ESXi host. Intrusions observed in December 2025 showed lateral movement, domain admin abuse, firewall rule manipulation, and staging of data for exfiltration.
CISA has now added CVE-2025-22225 to its Known Exploited Vulnerabilities (KEV) catalog, underscoring ongoing use by ransomware attackers.
Analyst Comments
Compromise of ESXi hypervisors significantly amplifies operational impact, allowing access to and potential encryption of dozens of VMs simultaneously. Organizations running ESXi 7.x and 8.x remain at high risk if patches and mitigations have not been applied. Therefore, clients are recommended to apply VMware patches from VMSA‑2025‑0004 across all ESXi, Workstation, and Fusion deployments. Enterprises are advised to assess their setups in order to reduce risk, as protecting publicly accessible management interfaces is a fundamental security best practice.
Sources
CVE-2025-22225 in VMware ESXi now used in active ransomware attacks
The Great VM Escape: ESXi Exploitation in the Wild
VMSA-205-004: VMware ESXi, Workstation, and Fusion updates address multiple vulnerabilities (CVE-205-22224, CVE-2025-22225, CVE-2025-22226)
Read More