Report
Malware Spotlight: Fog Ransomware
Aug 12, 2024
Arete Analysis
Tips
Cybersecurity Trends

Download The Report
Executive Summary
Since April 2024, Arete’s Incident Response (IR) team has responded to multiple engagements attributed to the Fog ransomware group. Engagements attributed to this group have been trending up since mid-June and through July 2024, accounting for nearly 20% of Arete’s ransomware and extortion engagements in July. The Fog ransomware group is especially noteworthy as it is one of the few threat actors specifically targeting one industry: education. Since April, Arete has observed that 70% of Fog victims have been education organizations. This spotlight explores the ransomware group’s observed behavior, background information on the threat actor, and statistics from Incident Response engagements, along with a technical analysis of Fog’s ransomware executable. Finally, we discuss security recommendations to better defend against this evolving cyber threat and mitigate the risk of financial and reputation losses.
Incident Response Data on the Fog Ransomware Group
The information below is based on Fog ransomware incidents investigated by Arete since April 2024. Our IR, Threat Intelligence, and Data Analytics teams work together to analyze key data points during every ransomware engagement and form real-time threat actor (TA) insights.
The median initial demand is $220,000.
The median ransom payment facilitated is $100,000.
36% of engagements involved data exfiltration, often using tools like MEGAsync and Filezilla.
Common initial access vectors include brute force attacks against remote desktop protocol (RDP) and compromised virtual private network (VPN) credentials.
Tools observed during investigations include CobaltStrike, Mimikatz, ngrok, WinRAR, AnyDesk, Advanced Port Scanner, and GMER, among others. The group demonstrates distinct skill in evading common anti-malware defenses.
The ransom note file name is commonly “readme.txt” and includes a link to a TOR site used for negotiations.
The group operates a data leak site (DLS) self-proclaimed as “The Fog Blog.”
Background
Fog ransomware was a prominent newcomer in the second quarter (Q2) of 2024 and demonstrated a noticeable trend of attacking entities in the education sector. Arete engagements involving Fog ransomware more than doubled during July 2024 compared to previous months.
Technical Analysis
Malware analysis revealed that Fog ransomware:
Supports multiple command-line arguments.
Encrypts files on the system and mounted shares.
Adds the following extensions to encrypted files: .fog, .ffog, or .flocked (e.g., file.docx.flocked).
Creates a ransom note with the following filename: readme.txt.
Self-identifies the group as Fog in the ransom note.
References a data leak site in the ransom note that, when accessed, self-identifies the group as Fog.
Kills a list of processes and services.
Maintains a list of whitelisted files and directories to make sure it will not render the system unusable, preventing recovery when running a decryptor.
Attempts to prevent system recovery by deleting the system’s volume shadow copies.
Creates a mutex during execution.
Creates a log file named DbgLog.sys.Execution Pattern/Arguments
Fog ransomware needs command line arguments to execute and encrypt files in the system. Command line arguments supported:
Command line arguments | Description |
|---|---|
-id | Key to decrypt ransomware configuration. |
-nomutex | Skip mutex check. |
-target | Specific location to encrypt files. |
-console | Creates a new console window for output. |
-size | File size threshold to encrypt. |
-log | Log the ransomware activity. |
-procoff | Presently unknown. |
-uncoff | Presently unknown. |
The ransomware will not execute in the system without the “-id” argument followed by a 6-character value that is unique in each engagement.
Execution of the ransomware to encrypt files:
Fog.exe -id [6-characters] Example: | ||
|---|---|---|
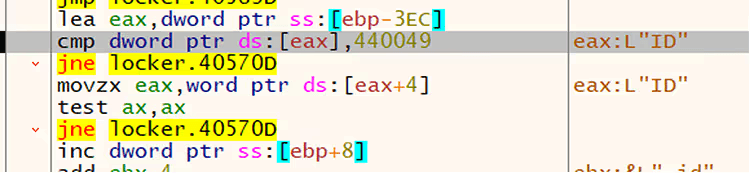
Figure 1. Code in the ransomware to check command line argument “-ID”
The ransomware uses the “-id” argument followed by a 6-character value to decrypt a JSON-based ransomware configuration information at runtime. Decrypted JSON field name and descriptions:
Name | Description |
|---|---|
RSAPubKey | Public key used in the file encryption process. |
LockedExt | Extension added to encrypted files. |
NoteFileName | Ransom note name. |
PathStopList | Excludes listed directories. |
FileMaskStopList | Excludes listed file extensions. |
ShutdownProcesses | Terminates list of processes. |
ShutdownServices | Terminates list of services. |
Stop Services and Processes
Before file encryption, the ransomware terminates a pre-determined list of processes and services to encrypt as many files as possible.
Process names:
“notepad.exe”, “calc.exe”, “*sql*” | ||
|---|---|---|
Service names:
“Dhcp”, “Dnscache”, “*sql*” | ||
|---|---|---|
Code in the ransomware showing this operation:
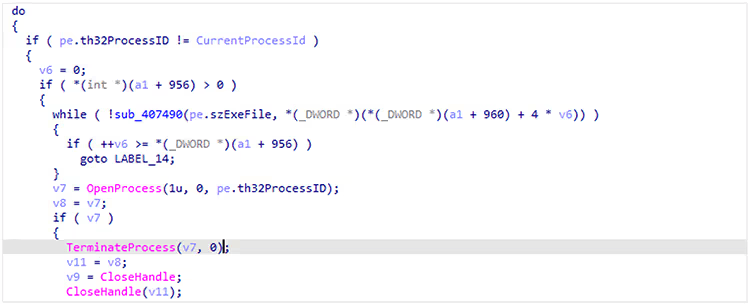
Figure 2. Process termination decompiled code
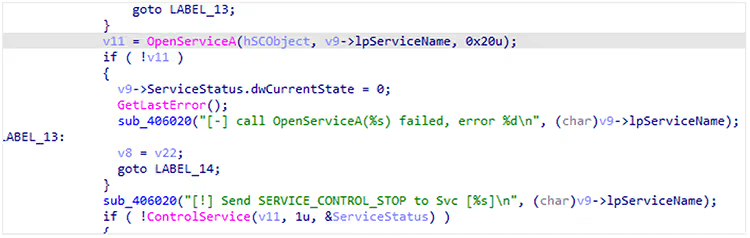
Figure 3. Service termination decompiled code
File and Directory Exclusions
The ransomware excludes system-related files and folders, ransomware-related files, and whitelisted extensions during encryption.
Excluded file extensions:
“*.exe”, “*.dll”, “*.lnk”, “*.sys” | ||
|---|---|---|
Excluded directories:
“tmp”, “winnt”, “Application Data”, “AppData”, “temp”, “thumb”, “$Recycle.Bin”, “System Volume Information”, “Windows”, “Boot” | ||
|---|---|---|
Inhibit System Recovery
Windows operating systems contain features that can help fix corrupted system files, including shadow copies, which are backups of files created by the Volume Shadow Copy Service (VSS). By deleting shadow copies, the ransomware can prevent victims from restoring files from backups, making it more difficult for them to recover their data without paying the ransom.
The ransomware deletes volume shadow copies before file encryption by starting the following process:
cmd.exe /c vssadmin delete shadows /all /quiet | ||
|---|---|---|
System Network Connections Discovery
Fog ransomware can enumerate network-mounted shares by scanning the network interfaces.
Data Encrypted for Impact
The ransomware initially finds available drives and then loads the files one by one using the Windows API FindFirstFileW and FindNextFileW. The ransomware generates random AES keys to encrypt the files, and after encrypting them, the keys are encrypted using a public RSA key. The resulting key is again encrypted and placed at the end of the file.
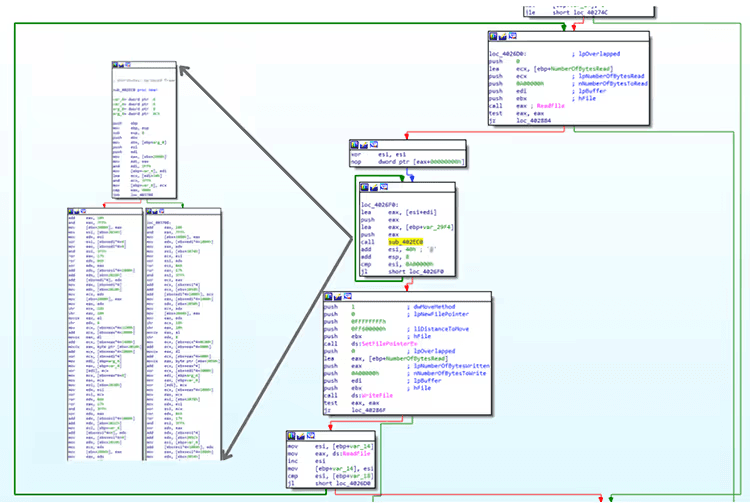
Figure 4. Data encryption code
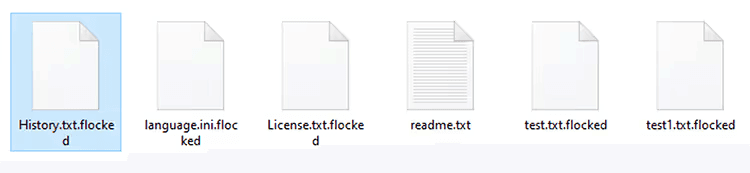
Figure 5. Extension added to the encrypted files
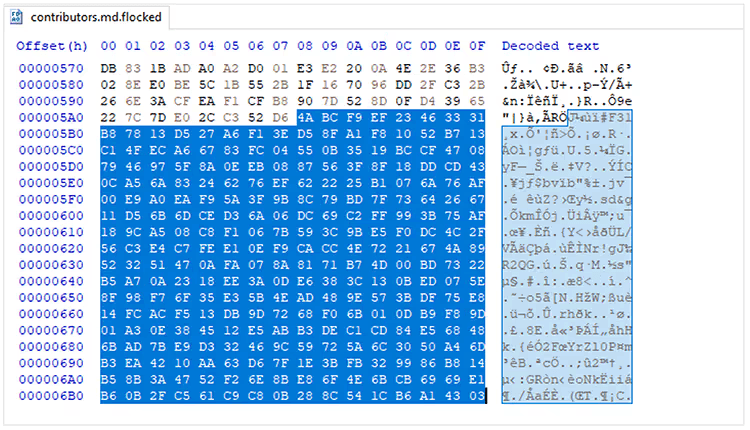
Figure 6. Encrypted AES key appended to encrypted file.
Fog ransomware extensions observed:
“.FOG”, “.FLOCKED”, “.FFOG” | ||
|---|---|---|
During execution, the ransomware creates a file named DbgLog.sys in the same directory and logs the ransomware activity. If the “-log” argument is used during ransomware execution, the ransomware creates and encrypts a lock_log.txt file under the C:\ProgramData directory. Encrypting the lock_log.txt file created might be an oversight in the ransomware code possibly indicating that the ransomware is still under development.
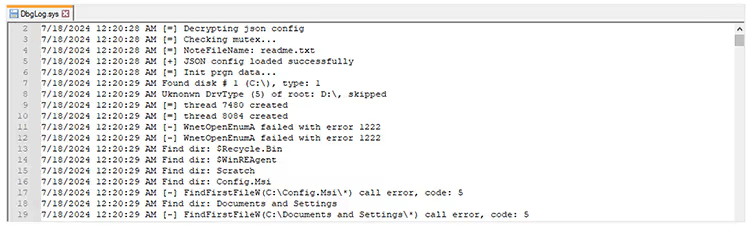
Figure 7. Log file created by the ransomware.
Upon successful execution, the ransomware creates ransom notes with the file name readme.txt.
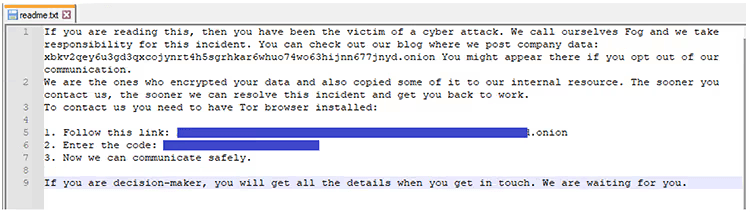
Figure 8. Fog ransom note
Ransom note content:
If you are reading this, then you have been the victim of a cyber attack. We call ourselves Fog and we take responsibility for this incident. You can check out our blog where we post company data: xbkv2qey6u3g3dqxcoyjnrt4h5sgrhkar6whuo74wo63hijnn677jnyd[.]onion You might appear there if you opt out of our communication. We are the ones who encrypted your data and also copied some of it to our internal resource. The sooner you contact us, the sooner we can resolve this incident and get you back to work. To contact us you need to have Tor browser installed:
| ||
|---|---|---|
Modify Registry
The ransomware did not perform any registry key modification.
Mutex
The mutex is the fundamental tool for managing shared resources between multiple threads or processes. Typically, ransomware uses a mutex to avoid reinfecting the victim system and causing multiple layers of encryption. The ransomware creates the following mutex value: XDLJgan1TkNkWfrQ78xVrust07YDq45X.
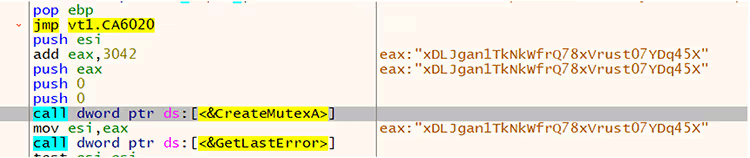
Figure 9. Mutex value created while debugging the ransomware
Network Activity
The ransomware did not try to communicate with a remote server other than encrypting data from mounted shares.
Indicators of Compromise
Indicator | Type | Context |
|---|---|---|
B6360765c786ceee0eb28bee64709172b4e2e066449968e011390be1afd8f36c515edfedadb458be0f569fc2bedb6c4139782516d6faf464b4881739e312e9fabbE67260804526323484f564eebeb6c99ed021b960b899ff788aed85bb7a9d75c3e44c342198e0ad8dd8c0f7bda19d4deb33f0d8355e3e78827505c3b858c82d54 | SHA256 hash | Fog ransomware |
C:\readme.txt | File path | Fog ransom note |
.fog, .flocked, .ffog | Extension | Encrypted file extensions |
vssadmin delete shadows /all /quiet | Process | Volume Shadow Copy deletion |
XDLJgan1TkNkWfrQ78xVrust07YDq45X | Mutex | Mutex value objects created by the Fog ransomware |
xbkv2qey6u3g3dqxcoyjnrt4h5sgrhkar6whuo74wo63hijnn677jnyd[.]onion | URL | TA data leak site (DLS) |
Data Leak Site
The ransom note contains a data leak site (DLS) that, when accessed, displayed the following page, self-identifying the group as Fog:
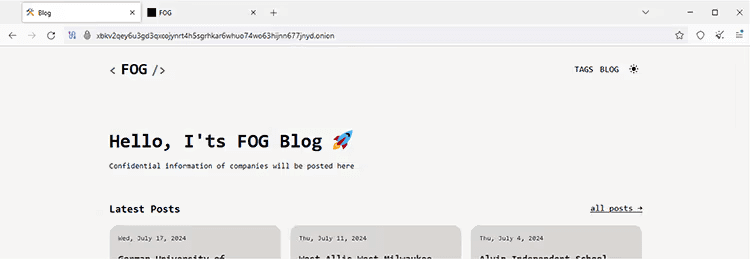
Figure 10. TOR DLS: xbkv2qey6u3gd3qxcojynrt4h5sgrhkar6whuo74wo63hijnn677jnyd[.]onion
Detection Mechanisms
Custom Detections and Blocking with Arete’s Arsenal
SentinelOne S1QL 1.0 query syntax (STAR rule):
Fog Ransomware
Akira Ransomware
Note: These threat hunting queries may need to be tuned for your specific network environment.
Yara
Recommended Mitigations
Utilize an endpoint detection and response (EDR) solution with the capability to halt detected processes and isolate systems on the network based on identified conditions.
Block any known attacker C2s in the firewall.
Implement multi-factor authentication on RDP and VPN to restrict access to critical network resources.
Eliminate unnecessary RDP ports exposed to the internet.
Block a high number of SMB connection attempts from one system to others in the network over a short period of time.
Perform periodic dark web monitoring to verify if data is available for sale on the black market.
Perform penetration tests.
Periodically patch systems and update tools.
Monitor connections to the network from suspicious locations.
Monitor downloads and uploads of files to file-sharing services outside standard work hours.
Monitor file uploads from domain controllers to the internet.
Monitor network scans from uncommon servers (e.g., RDP server).
Organizations can find the full list of US government-recommended ransomware prevention and mitigation guidance here: https://www.cisa.gov/stopransomware/ransomware-guide.
Arete provides data-driven cybersecurity solutions to transform your response to emerging cyber threats. Learn more.
References
At Arete, we envision a world without cyber extortion, where people, businesses, and governments can thrive. We are taking all that we know from over 8,000 engagements to inform our solutions and strengthen powerful tools to better prevent, detect, and respond to the cyber extortion threats of tomorrow. Our elite team of experts provides unparalleled capabilities to address the entire cyber threat lifecycle, from incident response and restoration to advisory and managed security services. To learn more about our solutions, visit www.areteir.com.
Back to Blog Posts
Article
Feb 20, 2026
Threat Actors Leveraging Gemini AI for All Attack Stages
State-backed threat actors are leveraging Google’s Gemini AI as a force multiplier to support all stages of the cyberattack lifecycle, from reconnaissance to post-compromise operations. According to the Google Threat Intelligence Group (GTIG), threat actors linked to the People’s Republic of China (PRC), Iran, North Korea, and other unattributed groups have misused Gemini to accelerate target profiling, synthesize open-source intelligence, identify official email addresses, map organizational structures, generate tailored phishing lures, translate content, conduct vulnerability testing, support coding tasks, and troubleshoot malware development. Cybercriminals are increasingly exploring AI-enabled tools and services to scale malicious activities, including social engineering campaigns such as ClickFix, demonstrating how generative AI is being integrated into both espionage and financially motivated threat operations.
What’s Notable and Unique
Threat actors are leveraging Gemini beyond basic reconnaissance, using it to generate polished, culturally nuanced phishing lures and sustain convincing multi-turn social engineering conversations that minimize traditional red flags.
In addition, threat actors rely on Gemini for vulnerability research, malware debugging, code generation, command-and-control development, and technical troubleshooting, with PRC groups emphasizing automation and vulnerability analysis, Iranian actors focusing on social engineering and malware development, and North Korean actors prioritizing high-fidelity target profiling.
Beyond direct operational support, adversaries have abused public generative AI platforms to host deceptive ClickFix instructions, tricking users into pasting malicious commands that deliver macOS variants of ATOMIC Stealer.
AI is also being integrated directly into malware development workflows, as seen with CoinBait’s AI-assisted phishing kit capabilities and HonestCue’s use of the Gemini API to dynamically generate and execute in-memory C# payloads.
Underground forums show strong demand for AI-powered offensive tools, with offerings like Xanthorox falsely marketed as custom AI but actually built on third-party commercial models integrated through open-source frameworks such as Crush, Hexstrike AI, LibreChat-AI, and Open WebUI, including Gemini.
Analyst Comments
The increasing misuse of generative AI platforms like Gemini highlights a rapidly evolving threat landscape in which state-backed and financially motivated actors leverage AI as a force multiplier for reconnaissance, phishing, malware development, and post-compromise operations. At the same time, large-scale model extraction attempts and API abuse demonstrate emerging risks to AI service integrity, intellectual property, and the broader AI-as-a-Service ecosystem. While these developments underscore the scalability and sophistication of AI-enabled threats, continued enforcement actions, strengthened safeguards, and proactive security testing by providers reflect ongoing efforts to mitigate abuse and adapt defenses in response to increasingly AI-driven adversaries.
Sources
GTIG AI Threat Tracker: Distillation, Experimentation, and (Continued) Integration of AI for Adversarial Use
Read More
Article
Feb 12, 2026
2025 VMware ESXi Vulnerability Exploited by Ransomware Groups
Ransomware groups are actively exploiting CVE‑2025‑22225, a VMware ESXi arbitrary write vulnerability that allows attackers to escape the VMX sandbox and gain kernel‑level access to the hypervisor. Although VMware (Broadcom) patched this flaw in March 2025, threat actors had already exploited it in the wild, and CISA recently confirmed that threat actors are exploiting CVE‑2025‑22225 in active campaigns.
What’s Notable and Unique
Chinese‑speaking threat actors abused this vulnerability at least a year before disclosure, via a compromised SonicWall VPN chain.
Threat researchers have observed sophisticated exploit toolkits, possibly developed well before public disclosure, that chain this bug with others to achieve full VM escape. Evidence points to targeted activity, including exploitation via compromised VPN appliances and automated orchestrators.
Attackers with VMX level privileges can trigger a kernel write, break out of the sandbox, and compromise the ESXi host. Intrusions observed in December 2025 showed lateral movement, domain admin abuse, firewall rule manipulation, and staging of data for exfiltration.
CISA has now added CVE-2025-22225 to its Known Exploited Vulnerabilities (KEV) catalog, underscoring ongoing use by ransomware attackers.
Analyst Comments
Compromise of ESXi hypervisors significantly amplifies operational impact, allowing access to and potential encryption of dozens of VMs simultaneously. Organizations running ESXi 7.x and 8.x remain at high risk if patches and mitigations have not been applied. Therefore, clients are recommended to apply VMware patches from VMSA‑2025‑0004 across all ESXi, Workstation, and Fusion deployments. Enterprises are advised to assess their setups in order to reduce risk, as protecting publicly accessible management interfaces is a fundamental security best practice.
Sources
CVE-2025-22225 in VMware ESXi now used in active ransomware attacks
The Great VM Escape: ESXi Exploitation in the Wild
VMSA-205-004: VMware ESXi, Workstation, and Fusion updates address multiple vulnerabilities (CVE-205-22224, CVE-2025-22225, CVE-2025-22226)
Read More
Article
Feb 5, 2026
Ransomware Trends & Data Insights: January 2026
Although Akira was once again the most active ransomware group in January, the threat landscape was more evenly distributed than it was throughout most of 2025. In December 2025, the three most active threat groups accounted for 57% of all ransomware and extortion activity; in January, the top three accounted for just 34%. Akira’s dominance also decreased to levels more consistent with early 2025, as the group was responsible for almost a third of all attacks in December but just 17% in January.
The number of unique ransomware and extortion groups observed in January increased slightly, to 17, up from 14 in December. It is too early to assess whether this trend will be the new normal for 2026. It is also worth noting that overall activity in January was lower than in previous months, consistent with what Arete typically observes at the beginning of a new year.
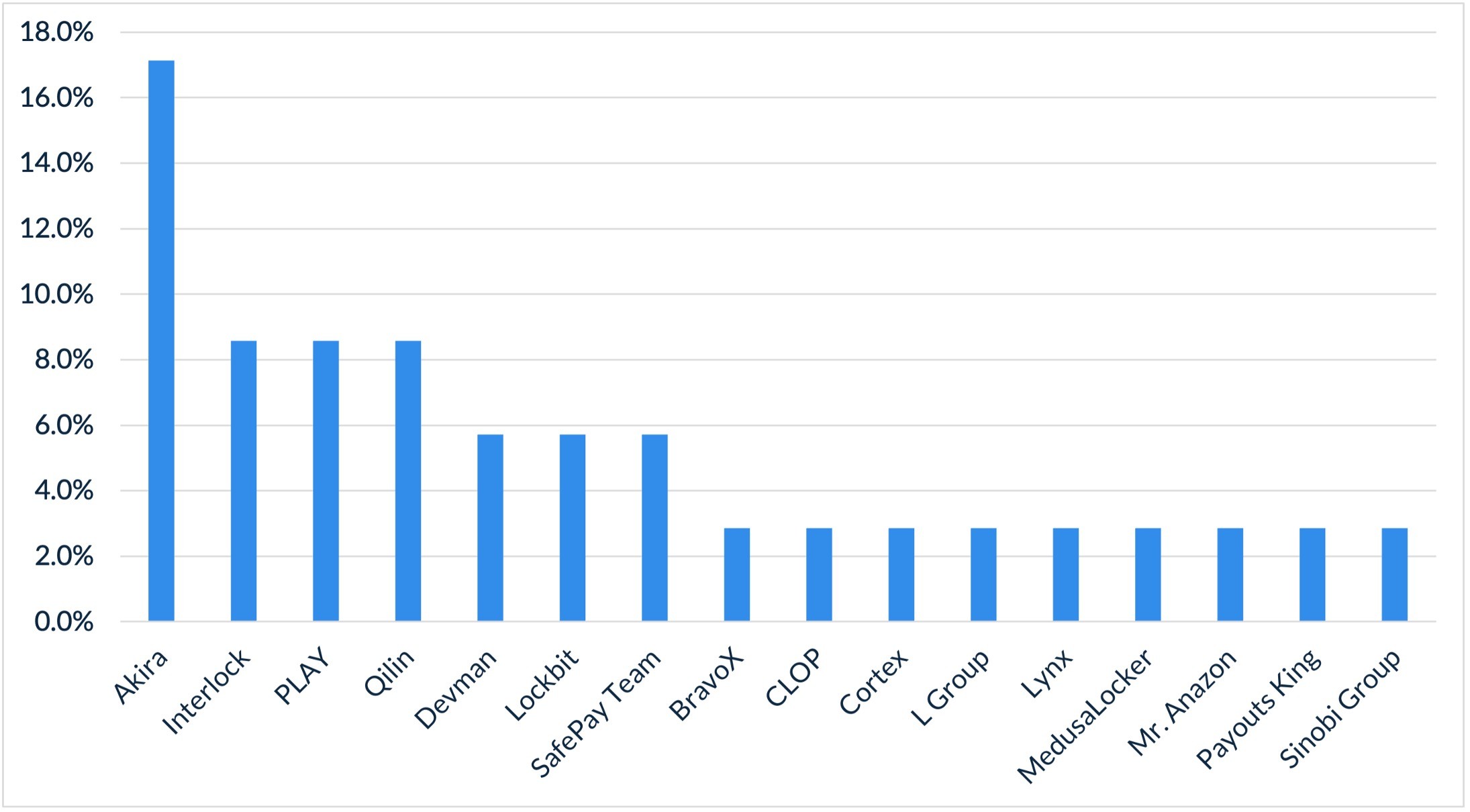
Figure 1. Activity from all threat groups in January 2026
Throughout the month of January, analysts at Arete identified several distinct trends behind the threat actors perpetrating cybercrime activities:
In January, Arete observed the reemergence of the LockBit Ransomware-as-a-Service (RaaS) group, which deployed an updated “LockBit 5.0” variant of its ransomware. LockBit first announced the 5.0 version on the RAMP dark web forum in early September 2025, coinciding with the group’s six-year anniversary. The latest LockBit 5.0 variant has both Windows and Linux versions, with notable improvements, including anti-analysis features and unique 16-character extensions added to each encrypted file. However, it remains to be seen whether LockBit will return to consistent activity levels in 2026.
The ClickFix social engineering technique, which leverages fake error dialog boxes to deceive users into manually executing malicious PowerShell commands, continued to evolve in unique ways in January. One campaign reported in January involved fake Blue Screen of Death (BSOD) messages manipulating users into pasting attacker-controlled code. During the month, researchers also documented a separate campaign, dubbed “CrashFix,” that uses a malicious Chrome browser extension-based attack vector. It crashes the web browser, displays a message stating the browser had "stopped abnormally," and then prompts the victim to click a button that executes malicious commands.
Also in January, Fortinet confirmed that a new critical authentication vulnerability affecting its FortiGate devices is being actively exploited. The vulnerability, tracked as CVE-2026-24858, allows attackers with a FortiCloud account to log in to devices registered to other account owners due to an authentication bypass flaw in devices using FortiCloud single sign-on (SSO). This recent activity follows the exploitation of two other Fortinet SSO authentication flaws, CVE-2025-59718 and CVE-2025-59719, which were disclosed in December 2025.
Source
Arete Internal
Read More
Article
Feb 2, 2026
New FortiCloud SSO Vulnerability Exploited
Fortinet recently confirmed that its FortiGate devices are affected by a new critical authentication vulnerability that is being actively exploited. The vulnerability, tracked as CVE-2026-24858, allows attackers with a FortiCloud account to log in to devices registered to other account owners due to an authentication bypass flaw in devices using FortiCloud single sign-on (SSO). CISA added the vulnerability to its Known Exploited Vulnerabilities catalogue and gave federal agencies just three days to patch, which requires users to upgrade all devices running FortiOS, FortiManager, FortiAnalyzer, FortiProxy, and FortiWeb to fixed versions. This recent activity follows the exploitation of two other SSO authentication flaws, CVE-2025-59718 and CVE-2025-59719, which were disclosed last month.
What’s Notable and Unique
There are strong indications that much of the recent exploitation activity was automated, with attackers moving from initial access to account creation within seconds.
As observed in December 2025, the attackers’ primary target appears to be firewall configuration files, which contain a trove of information that can be leveraged in future operations.
The threat actors in this campaign favor innocuous, IT-themed email and account names, with malicious login activity originating from cloud-init@mail[.]io and cloud-noc@mail[.]io, while account names such as ‘secadmin’, ‘itadmin’, ‘audit’, and others are created for persistence and subsequent activity.
Analyst Comments
This is an active campaign, and the investigation into these attacks is ongoing. Organizations relying on FortiGate devices should remain extremely vigilant, even after following patching guidance. With threat actors circumventing authentication, it’s crucial to monitor for and alert on anomalous behavior within your environment, such as the unauthorized creation of admin accounts, the creation or modification of access policies, logins outside normal working hours, and anything that deviates from your security baseline.
Sources
Administrative FortiCloud SSO authentication bypass
Multiple Fortinet Products’ FortiCloud SSO Login Authentication Bypass
Arctic Wolf Observes Malicious Configuration Changes On Fortinet FortiGate Devices via SSO Accounts
Arctic Wolf Observes Malicious SSO Logins on FortiGate Devices Following Disclosure of CVE-2025-59718 and CVE-2025-59719
Read More